Sunday, March 5, 2017
What Is IP Spoofing And Denial Of Service DOS Attack
What Is IP Spoofing And Denial Of Service DOS Attack
 Short Bytes: IP Spoofing and Denial of Service are the two most famous attacks that an intruder launches to attack a particular target. While IP Spoofing targets the routing table of the network, DOS attack aims at burning out the resources of the target computer.
Short Bytes: IP Spoofing and Denial of Service are the two most famous attacks that an intruder launches to attack a particular target. While IP Spoofing targets the routing table of the network, DOS attack aims at burning out the resources of the target computer.IP Spoofing attack and DOS (Denial of Service) attacks often go hand in hand. So, to understand how they work, we will go at the basic level of computer networks and try to analyze the technicality behind this attack.
What is IP spoofing?
When a computer outside of your network pretends to be a trusted computer within the network, then, this action by the attacker is called IP Spoofing.To gain access to your network, an outside computer must gain one of your trusted IP addresses from the network. So, the attacker might use an IP address within the range of your network. Or, on the other hand, the attacker can also use an authorized external IP address that is trusted within the network.
These IP addresses could be so trusted that they can also have special privileges to the important resources on the network.
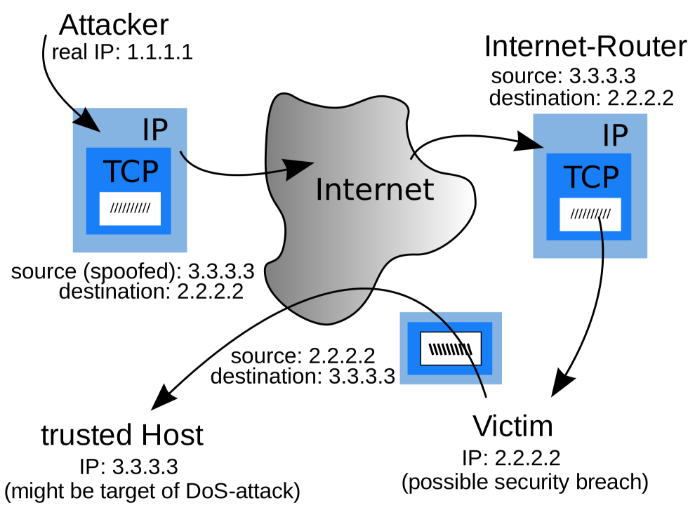
Different ways of IP spoofing?
- Injection of data or a set of commands into an existing stream of data that is passed in between a client and server application.
- Injection of data or commands into a peer-to-peer network connection.
Once the routing table is changed, the attacker starts receiving all the data from the network to the spoofed IP address. He/she can even reply to those packets just like any other trusted user.
Denial of Service (DOS) attacks:
You can think DoS attacks as a modified version of the IP spoofing. In DOS attack, unlike IP spoofing, the attacker does not worry about receiving any response from the targeted host.The attacker floods the system with a lot of requests such that the system becomes busy in returning replies.
If we get into the technicality of this attack, then, the targeted host receives a TCP SYN and returns a SYN-ACK. After sending the SYN-ACK, the targetted user waits for the reply to complete the TCP handshake that never happens.
So, each of these wait states utilizes the system resource and eventually the host cannot reply to other legitimate requests.
Available link for download